Around 1000 Untracked Cybersecurity Vulnerabilities Potentially Exploited by China and Russia
Core Concepts
There are around 1000 exploitable cybersecurity vulnerabilities that have not been tracked or documented by MITRE, NIST, and other major vulnerability tracking organizations, but may have been discovered and exploited by adversaries like China and Russia.
Abstract
The article discusses a set of cybersecurity vulnerabilities that have not been assigned CVE (Common Vulnerabilities and Exposures) identifiers by MITRE and NIST, the leading vulnerability tracking organizations. These vulnerabilities have instead been mapped to other vulnerability databases like CNVD, CNNVD, and BDU, which are less widely used globally.
The author, representing the A.R.P. Syndicate, a cybersecurity intelligence company, claims that their Exploit Observer's VEDAS (Vulnerability & Exploit Data Aggregation System) has identified around 1000 such vulnerabilities. They argue that while the CVE ecosystem is improving, it still misses a significant number of real-world vulnerabilities that may have been discovered and exploited by adversaries like China and Russia.
The article emphasizes that the false negatives (missed vulnerabilities) are more concerning than false positives (incorrectly identified vulnerabilities) in automated security systems. It encourages independent researchers to test and verify the findings, and report any discrepancies.
The author also highlights that China and Russia's domestic vulnerability tracking systems, like CNITSEC and FSTEC, may have better coverage of the global vulnerability ecosystem than is publicly revealed. This poses a concern for security teams that rely primarily on the CVE system.
The article introduces the Exploit Observer's VEDAS as a solution, which aggregates and interprets exploit and vulnerability data from various sources. It claims that VEDAS has a unique scoring algorithm that focuses on how easily an adversary can exploit a vulnerability, rather than just the severity.
Over a 1000 vulnerabilities that MITRE & NIST ‘might’ have missed but China or Russia did not.
Stats
There are around 1000 exploitable cybersecurity vulnerabilities that MITRE, NIST, and other major vulnerability tracking organizations have missed.
The CVE ecosystem has over 370+ CNA (CVE Numbering Authority) partners generating input 24/7, and the CVE database is constantly improving.
China and Russia's domestic vulnerability tracking systems, like CNITSEC and FSTEC, may have better coverage of the global vulnerability ecosystem than is publicly revealed.
Quotes
"CVE ecosystem has 370+ CNA partners generating invaluable input 24x7. A lot of changes happen everyday in the CVE Database & it's only getting better with time."
"CVE is the worst vulnerability framework (Except for all the others) — From Vulncon 2024"
"China's New Vuln System — From Vulncon 2024"
Key Insights Distilled From
by Ayush Singh at blog.arpsyndicate.io 05-18-2024
https://blog.arpsyndicate.io/over-a-1000-vulnerabilities-that-mitre-nist-might-have-missed-but-china-or-russia-did-not-871b2364a526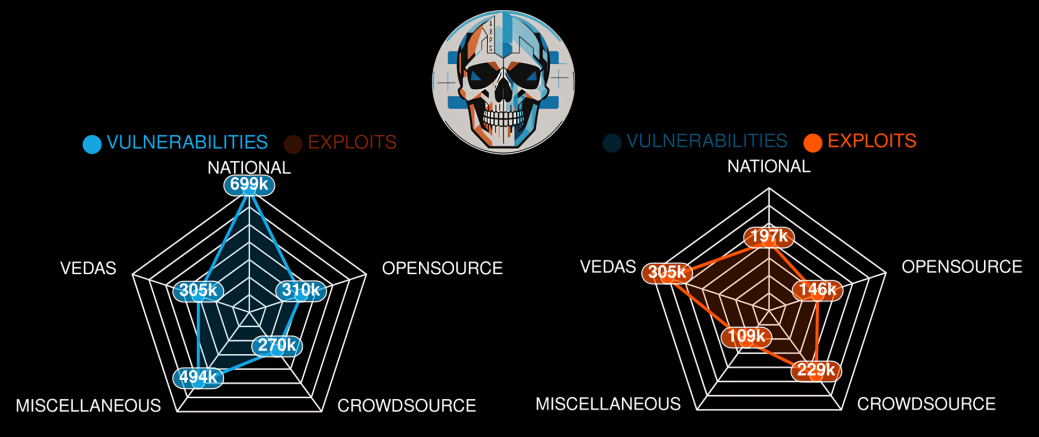
Deeper Inquiries
How can the cybersecurity community work together to improve the coverage and accuracy of vulnerability tracking systems globally?
Collaboration is key in enhancing the coverage and accuracy of vulnerability tracking systems globally. The cybersecurity community can work together by sharing threat intelligence, collaborating on research projects, and participating in information-sharing platforms. By pooling resources and expertise, organizations can collectively identify and address vulnerabilities that may have been missed by existing systems. Additionally, promoting transparency and accountability within the community can help in validating and verifying vulnerability data, leading to more reliable tracking systems.
What are the potential implications of adversaries like China and Russia having access to a larger pool of untracked vulnerabilities, and how can organizations mitigate this risk?
The implications of adversaries like China and Russia having access to untracked vulnerabilities are significant. They could potentially exploit these vulnerabilities to launch cyber attacks, gather sensitive information, or disrupt critical infrastructure. To mitigate this risk, organizations should prioritize proactive security measures such as continuous monitoring, timely patching, and implementing robust cybersecurity protocols. Additionally, fostering strong partnerships with cybersecurity experts, sharing threat intelligence, and staying informed about emerging vulnerabilities can help organizations stay ahead of potential threats posed by adversaries with access to untracked vulnerabilities.
What innovative approaches or technologies could be developed to enhance the vulnerability discovery and tracking process, beyond the current limitations of the CVE system?
To enhance vulnerability discovery and tracking beyond the limitations of the CVE system, innovative approaches and technologies can be explored. One approach could involve leveraging artificial intelligence and machine learning algorithms to automate the identification and classification of vulnerabilities based on various data sources. Additionally, the development of decentralized vulnerability databases that allow for real-time collaboration and information sharing among security researchers could improve the accuracy and coverage of vulnerability tracking. Furthermore, integrating blockchain technology to create a tamper-proof and transparent system for tracking vulnerabilities could enhance the overall security posture of organizations and the cybersecurity community.
0
