How Lava Lamps Secure the Internet
Core Concepts
Lava lamps are utilized by Cloudflare to generate encryption keys and enhance internet security.
Abstract
Introduction:
Lava lamps, once a popular decor item, now play a crucial role in internet security.
Cloudflare, a major web hosting company, uses lava lamps to protect websites from hackers.
Lava Lamp Security:
Cloudflare manages 20% of the internet's primary traffic and hosts numerous websites.
A wall of 100 lava lamps at Cloudflare's headquarters generates encryption keys for web traffic.
The camera above the lava lamp wall captures positions of the lava bubbles to create encryption keys.
Importance of Random Information:
The randomness produced by lava lamps is essential for building secure encryption.
Cloudflare openly discusses their use of lava lamps as a security measure.
How A Wall of Lava Lamps Is Protecting The Internet
Stats
Cloudflare manages roughly 20% of the internet's primary traffic.
A wall with approximately 100 lava lamps at Cloudflare's headquarters generates encryption keys for web traffic.
Quotes
"Lava lamps are working tirelessly to keep the internet safe from hackers."
"The secret is not in the lava lamps themselves but rather what they produce — a constant stream of random information."
Key Insights Distilled From
by Grant Piper at grantpiperwriting.medium... 03-21-2024
https://grantpiperwriting.medium.com/how-a-wall-of-lava-lamps-is-protecting-the-internet-c7b773b251ee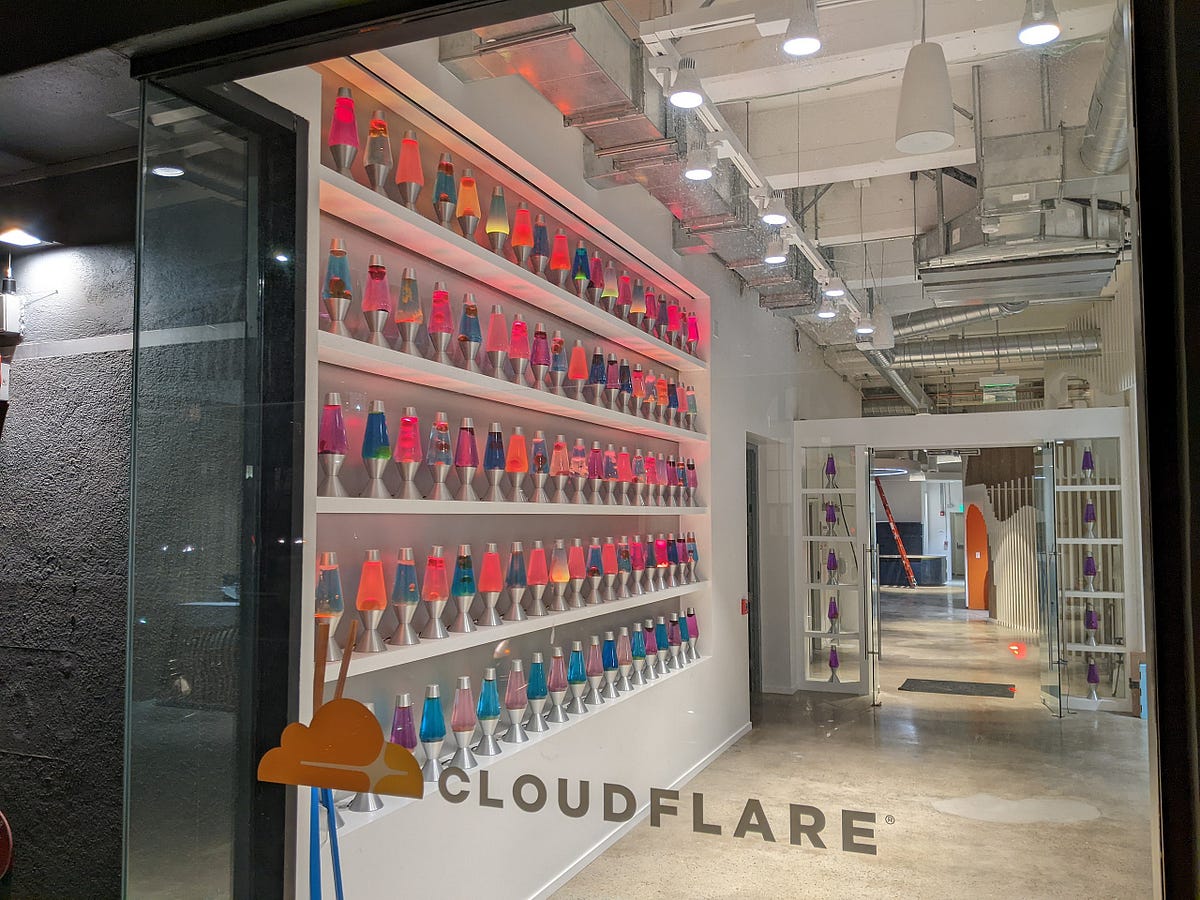
Deeper Inquiries
How can other industries adopt unconventional methods like using lava lamps for enhancing security?
Other industries can adopt unconventional methods for enhancing security by thinking outside the box and exploring unique solutions that may not be typical in cybersecurity. One way is to look at physical phenomena or processes that are inherently random, such as the movement of lava lamp bubbles, and use them to generate encryption keys or create secure systems. By embracing creativity and innovation, industries can find new ways to protect their data and networks from cyber threats.
What potential drawbacks or vulnerabilities could arise from relying on such unique security measures?
While using unconventional security measures like lava lamps can be effective in generating random information for encryption keys, there are potential drawbacks and vulnerabilities to consider. One concern is the reliability of these systems over time - if a component fails or malfunctions, it could compromise the entire security infrastructure. Additionally, there may be limitations in scalability or compatibility with existing technologies when implementing such unique measures across different platforms or environments. Moreover, attackers might eventually find ways to exploit weaknesses in these non-traditional security methods.
How does the concept of randomness in generating encryption keys challenge traditional cybersecurity practices?
The concept of randomness in generating encryption keys challenges traditional cybersecurity practices by introducing a new layer of complexity and unpredictability into securing data transmissions. Traditional practices often rely on algorithms or predetermined patterns to create encryption keys, which could potentially be vulnerable to sophisticated attacks targeting those predictable patterns. By leveraging randomness through sources like lava lamp movements, organizations can enhance their cryptographic strength by creating truly unpredictable keys that are harder for hackers to crack using conventional means. This shift towards randomness disrupts established norms in cryptography but offers a more robust defense against evolving cyber threats.
0
